HackTheBox : Delivery Walkthrough

Concepts Learnt :
- Enumeration
- HelpDesk Exploit
- Password Cracking Using HashCat
Steps to Enumerate :
Run an Nmap Scan to find all the open ports!
Command : nmap 10.10.10.222 -A
10.10.10.222 IP of the Server
-A This options makes Nmap make an effort in identifying the target OS,services and the versions. It also does traceroute and applies NSE scripts to detect additional information.
-vv Defines level 2 verbosity for the scan

We see that there are 2 ports open :
80/tcp- HTTP port
22/tcp- SSH port
Lets explore the website on port 80
Go to 10.10.10.222:80 in the browser
A simple webpage with a contact us button!
Let explore the site more!
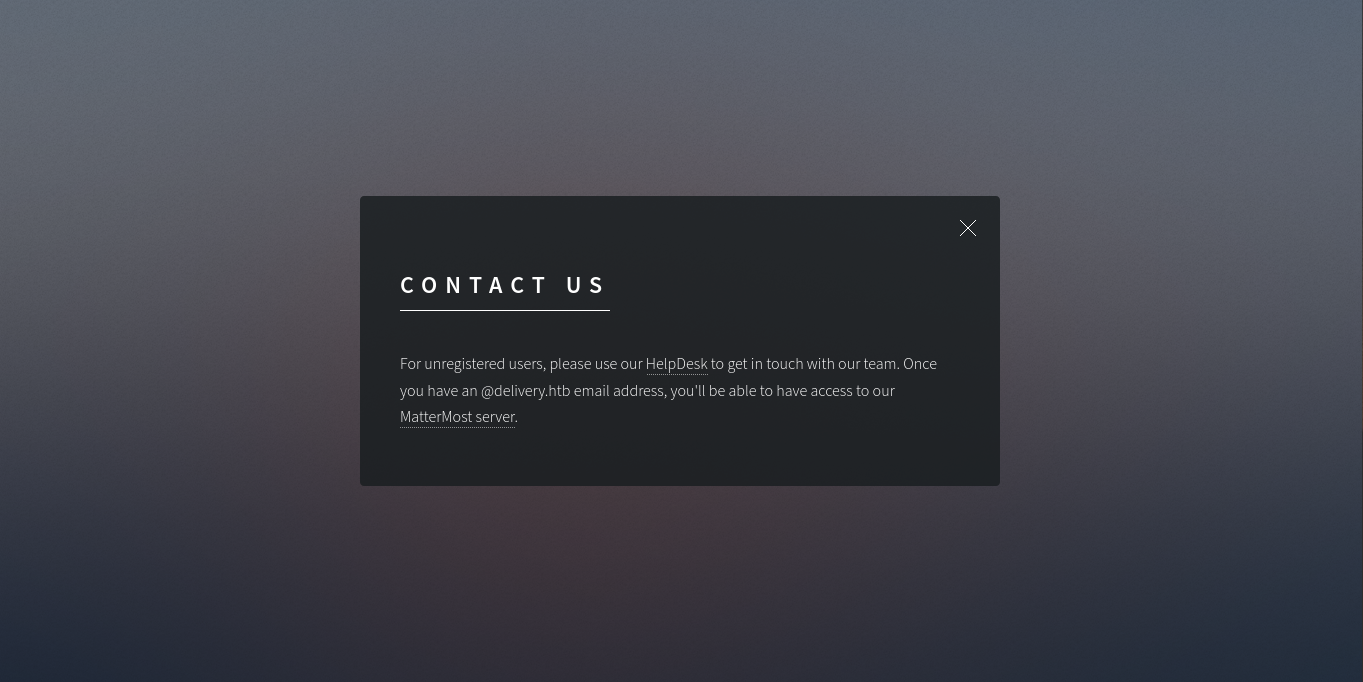
Help Desk and MatterMost Server are two possible links to navigate to! But we can’t directly! We need to add these pages to the /etc/hosts file to resolve them!
Command : sudo nano /etc/hosts
Add the following lines below the user IP!
10.10.10.222 delivery.htb helpdesk.delivery.htb

Now we can access these pages!
Loading the Helpdesk page, we can either create a ticket or check a ticket.

Lets open a new ticket!
Fill out the details for the form!

You will see a result page showing you your ticket id and an email id [ticketid]@delivery.htb.
We can use this to sign up for the MatterMost Server!
Click on Create an Account!
Fill in the email id you received from the ticket we generated above!

Once you create an account you will receive an update on your ticket with the verification!
To check your ticket go back to the ticket center and fill in the test email id you used before and the ticket number!
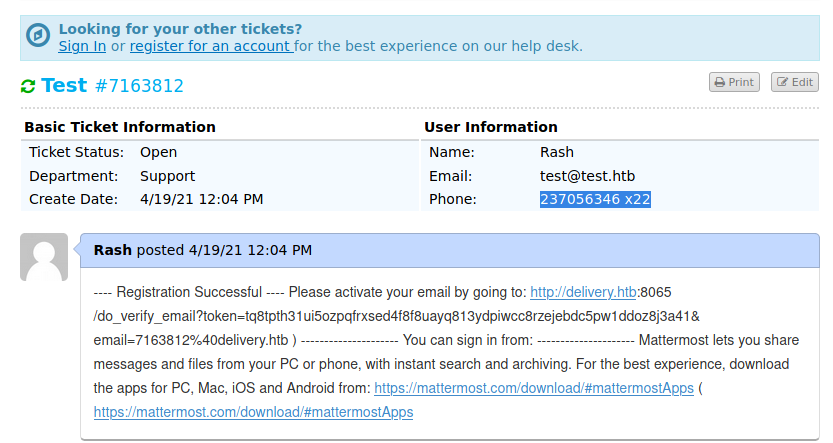
Select and copy the verification token into the browser and now we can log in!
Once logged in we can see all the chat in the internal channel!
You will find the username and password for the mail server here as well as a Clue to crack the future passwords!
The clue will be used below to crack the passwords!
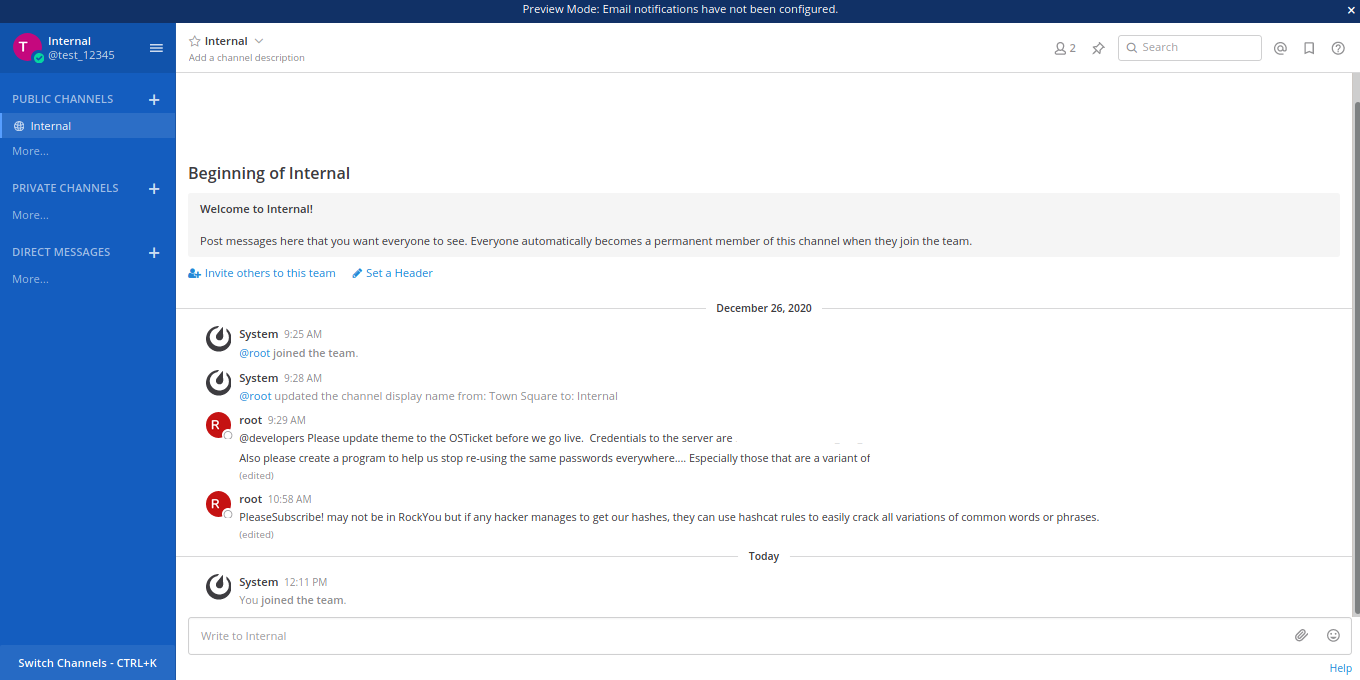
Now lets use this to ssh into the system!
Command: ssh [username from above!]@10.10.10.222
Type in the password!
Command : ls

We got our first user Flag!
Command : cat user.txt
Now we know that since the mattermost site has a user login system it is most likely it stores in all the possible credentials in a database. The most common database for any website is MySql. But we need credentials for the database.
Checking the folder system we find there is a folder mattermost under /opt/
And we have a config folder under it
Now change Directory to config
Command : cd config
And we have a .json file that can help with the credentials!
We find the creds under “Sql Settings”
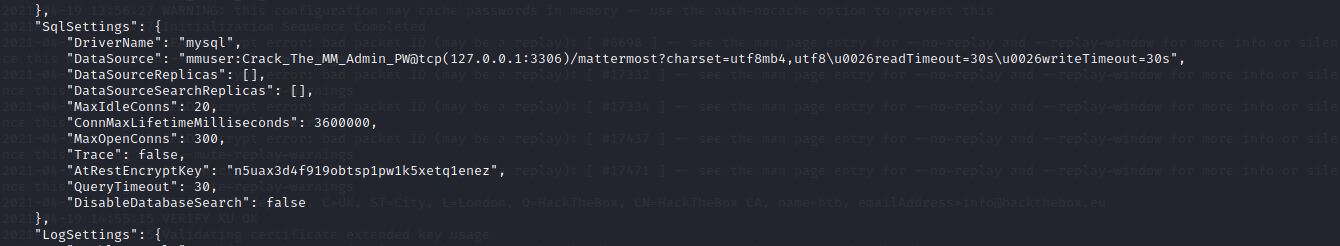
Now logging into the SQL database :
Command : mysql -u mmuser -pCrack_The_MM_Admin_PW

Now we can check all possible tables in the Database :
Command : SELECT * FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_TYPE=’BASE TABLE’;
We get all possible tables in the database listed

However we are interested in the users table
Command : SELECT Username,Password,Email FROM Users;
We get the list of all username password and email id!

We can see there is a root username and password, but the password is as hash!
We will have to crack it out using hashcat!
Open a separate terminal and create a folder to store in all the possible files generated from hashcat and used in hashcat.
I created a folder named crack.
And created a file named hash and copied the root hash from the database above.
Next I created a file name clue to store the clue we got from the chat above!

Now we will generate a possible wordlist using the clue above :
Command : hashcat -r /usr/share/hashcat/rules/best64.rule — stdout clue > password.txt
And we get an output file as password.txt with a list of all possible combinations!

Now we will run our hash against this password list.
Command : hashcat -m 3200 hash password.txt
And we get the root password!

Go back to the ssh terminal and switch user to root.
Command : su root
And enter in the password and you are logged in as root!
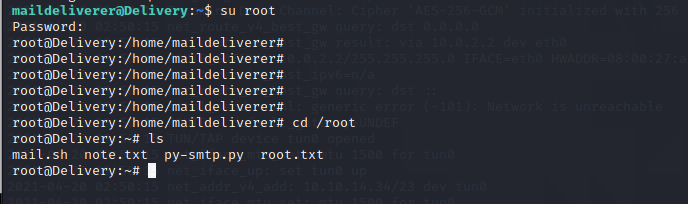
Now change directory to the root folder
Command : cd /root
And you get the second Flag in root.txt !
This was a fun room to work on. Hope you enjoyed!










Comments
Post a Comment